This plugin allows projects to run builds with specified authorization.
This plugin provides following features:
- You can configure projects to have their builds run with specified authorization.
- This is an implementation of QueueItemAuthenticator.
- Provides following ways to specify authorization.
- Run as the user who triggered the build.
- Does not work for scheduled, or polled builds.
- Configuring projects are allowed only to users with the BUILD permission.
- Run as anonymous.
- Run as the specified user.
- You are requested to enter the password of the specified user except in the following cases:
- You are an administrator.
- You are the specified user.
- The specified user is not changed from the last configuration, and "No need for re-authentication" is checked.
- This can be a security risk
- Configuring projects are allowed only to administrators and the user configured as the authorization.
- "Don't restrict job configuration" allows other users (with the CONFIGURE permission) to configure the project. Ensure that only appropriate users have CONFIGURE permission for that project.
- You are requested to enter the password of the specified user except in the following cases:
- Run as SYSTEM
- This is provided only to cancel the global configuration. SYSTEM authorization is often considered as "unconfigured", features provided by plugins may treat it as anonymous.
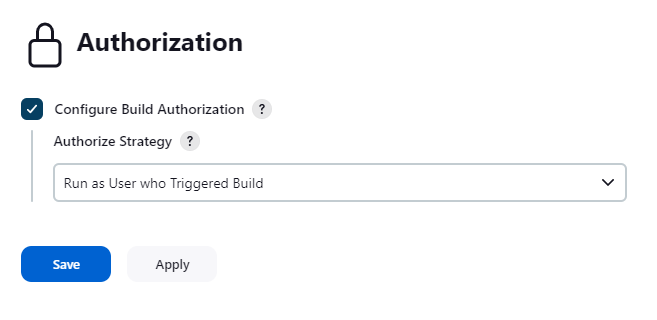
- Run as the user who triggered the build.
- Provides an extension point to add new ways to specify authorization.
- The plugin adds "Access Control for Builds" in "Manage Jenkins" > "Configure Global Security". Adding "Configure Build Authorizations in Project Configuration" enables Authorize Project plugin.
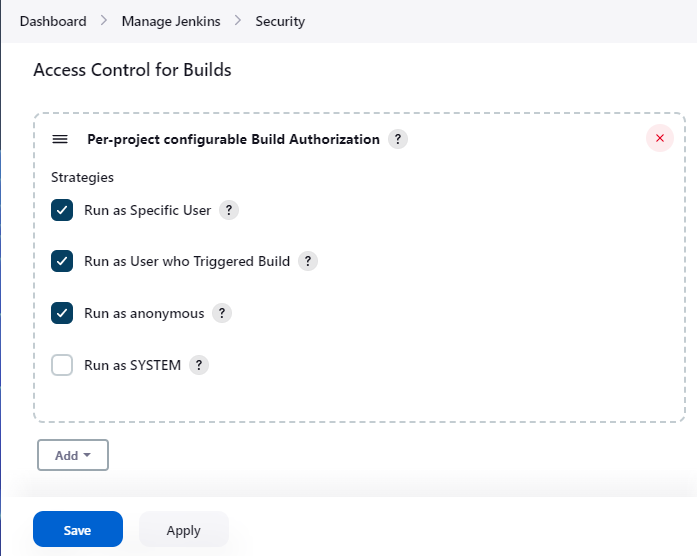
- You can also disable specific strategies in this page. Disabled strategies are never used for authorization.
- A new side bar menu "Authorization" will appear in project pages.
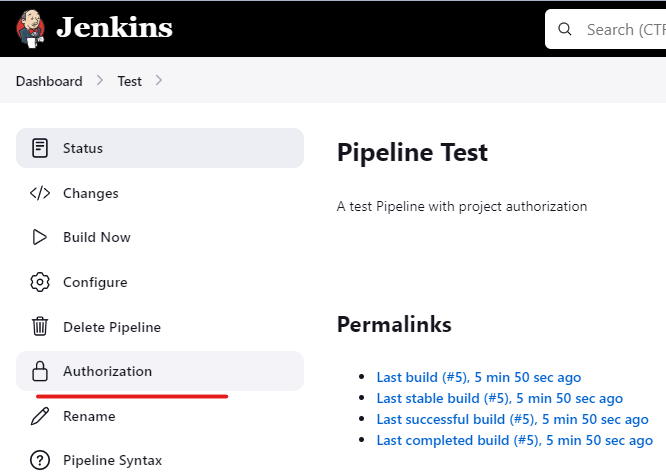
- You can select how to authorize builds of the project in the "Authorization" page.
- When selecting "Run as Specific User", you can enter User ID with whose authorization builds will run. If you enter a user ID except yourself and have no administrative privilege, you are required to enter the password of that user.
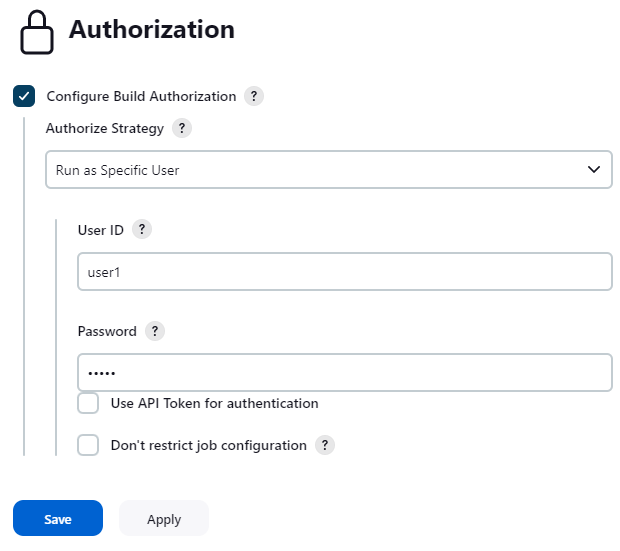
- You can also use API token, especially for non password-based security realms.
- Configuring project settings by unauthorized users are forbidden when you configure the authorization for the project. See What's this? for details.

A new way to authorize projects can be added by extending AuthorizeProjectStrategy, overriding the following method:
public abstract Authentication authenticate(
hudson.model.AbstractProject<?, ?> project,
hudson.model.Queue.Item item
);
Use AuthorizeProjectStrategyDescriptor for Descriptor. If you want to provide global configuration properties, do as following:
global-security.jellyis displayed in "Configure Global Security" page.- Override
AuthorizeProjectStrategyDescriptor#configureFromGlobalSecurityto save configuration.
To report a bug or request an enhancement to this plugin please create a ticket in JIRA (you need to login or to sign up for an account). Also have a look on How to report an issue
- See GitHub Releases for the recent releases
- See the Changelog Archive for version 1.3.0 and older